Finding Exploit Using The Searchsploit In Kali Linux HacCoders
Add this topic to your repo. To associate your repository with the website-hacking topic, visit your repo's landing page and select "manage topics." GitHub is where people build software. More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects.
Encontrar o Exploit offline usando o Searchsploit no Kali Linux Acervo Lima
Kali Linux, with its BackTrack lineage, has a vibrant and active community. There are active Kali forums, IRC Channel, Kali Tools listings, an open bug tracker system, and even community provided tool suggestions. All the tools you need. The Kali Linux penetration testing platform contains a vast array of tools and utilities.

How To Use ExploitDB To Find And Exploit Vulnerabilities In Kali Linux Systran Box
Step 1: Start PostgreSQL database server. The PostgreSQL database is installed but not started on Kali Linux. Start the service using the following command. sudo systemctl enable --now postgresql. Confirm that the service is started and set to run on boot. $ systemctl status postgresql@*-main.service.

Hacking with Kali Linux Web service hacking YouTube
To help interactive with various parts of the Metasploit configuration there is msfdb: kali@kali:~$ sudo msfdb. Manage the metasploit framework database. msfdb init # start and initialize the database. msfdb reinit # delete and reinitialize the database. msfdb delete # delete database and stop using it.

Encontrar Exploits en Kali Linux utilizando Searchsploit Alonso Caballero / ReYDeS
Method 1. To begin, we'll use Kali Linux's automated tool sqlmap to perform the SQL injection. I'm using testphp.vulnweb.com. It's a demo site for the Acunetix Web Vulnerability Scanner. It's critical to have a path to the website you're attempting to attack.

How To Search Exploit Using Kali LInux "Searchsploit" YouTube
Websploit is an automatic vulnerability assessment, web scanner and ex-. ploiter tool. It is python command line tool that is composed on modu-. lar structure pretty similar to Metasploit. There are currently 7 mod-. ules. The command line does not accept any options. User just get into.
Cara DDoS Attack dengan Golden Eye di Kali Linux Exploit Abdur Rozak
Let's start with a simple attack. If we have the username and password that we expect a system to have, we can use Hydra to test it. Here is the syntax: $ hydra -l
HowTo Importing ExploitDB Exploits into Metasploit in Kali Linux The EASY Way. YouTube
1. Install Metasploit Using Repository. First, you need to update the local package repository and then install Metasploit by running the apt commands as shown. $ sudo apt update. $ sudo apt install metasploit-framework. Install Metasploit Framework in Kali Linux. 2.
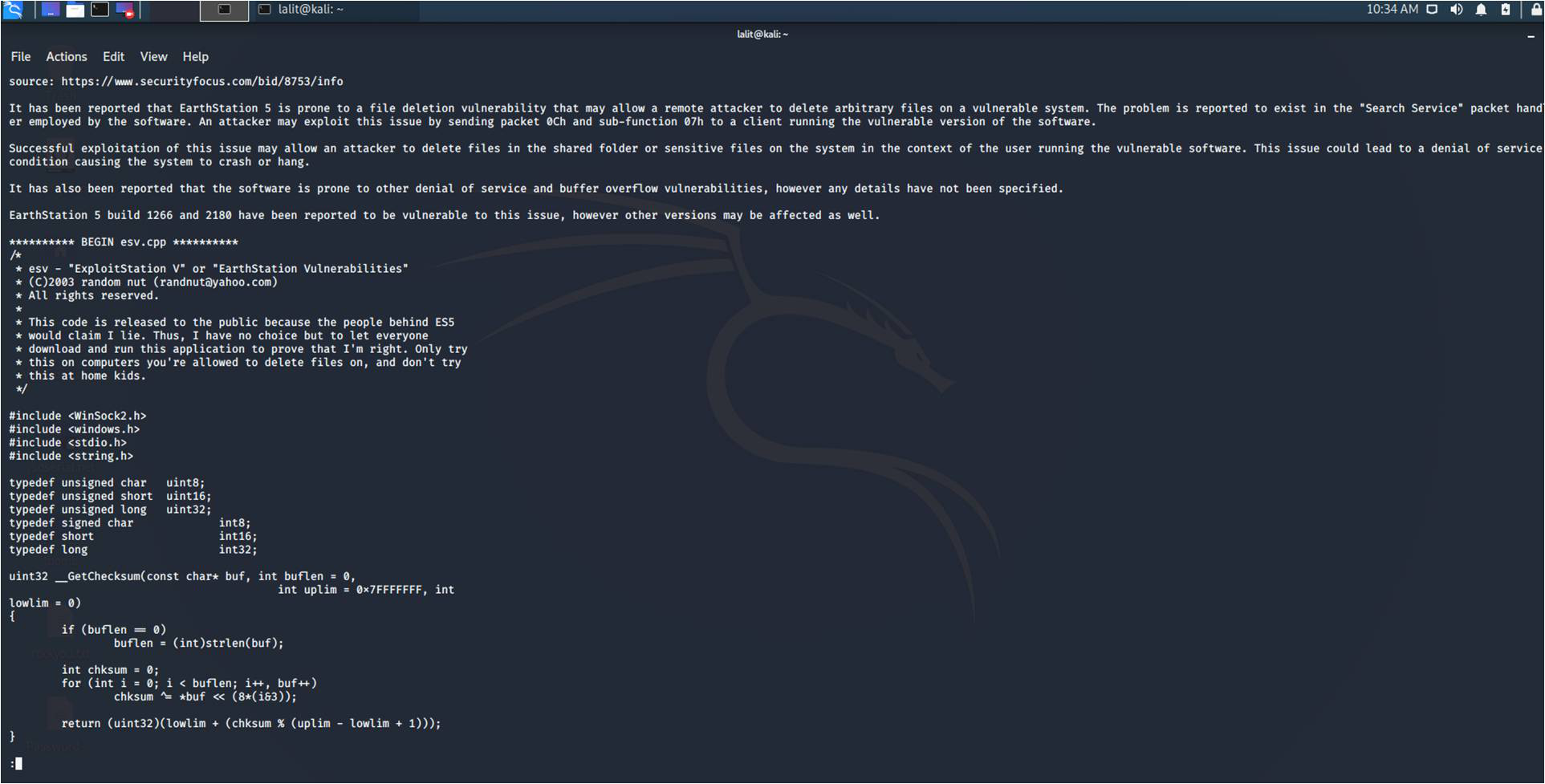
Encontrar Exploit fuera de línea usando Searchsploit en Kali Linux Barcelona Geeks
Kali Linux: Software: WPScan: Other: Privileged access to your Linux system as root or via the sudo command. Conventions # - requires given linux commands to be executed with root privileges either directly as a root user or by use of sudo command $ - requires given linux commands to be executed as a regular non-privileged user

How to exploit OpenSSL Heart Bleed on kali linux YouTube
Metasploit adalah sebuah kerangka kerja (framework) yang digunakan untuk mengembangkan, menguji, dan meluncurkan serangan keamanan komputer. Ini mencakup berbagai alat, modul, dan eksploit yang.

19 Kali Linux Gcc exploit derleme ( SızmaTestleri Eğitimi ) YouTube
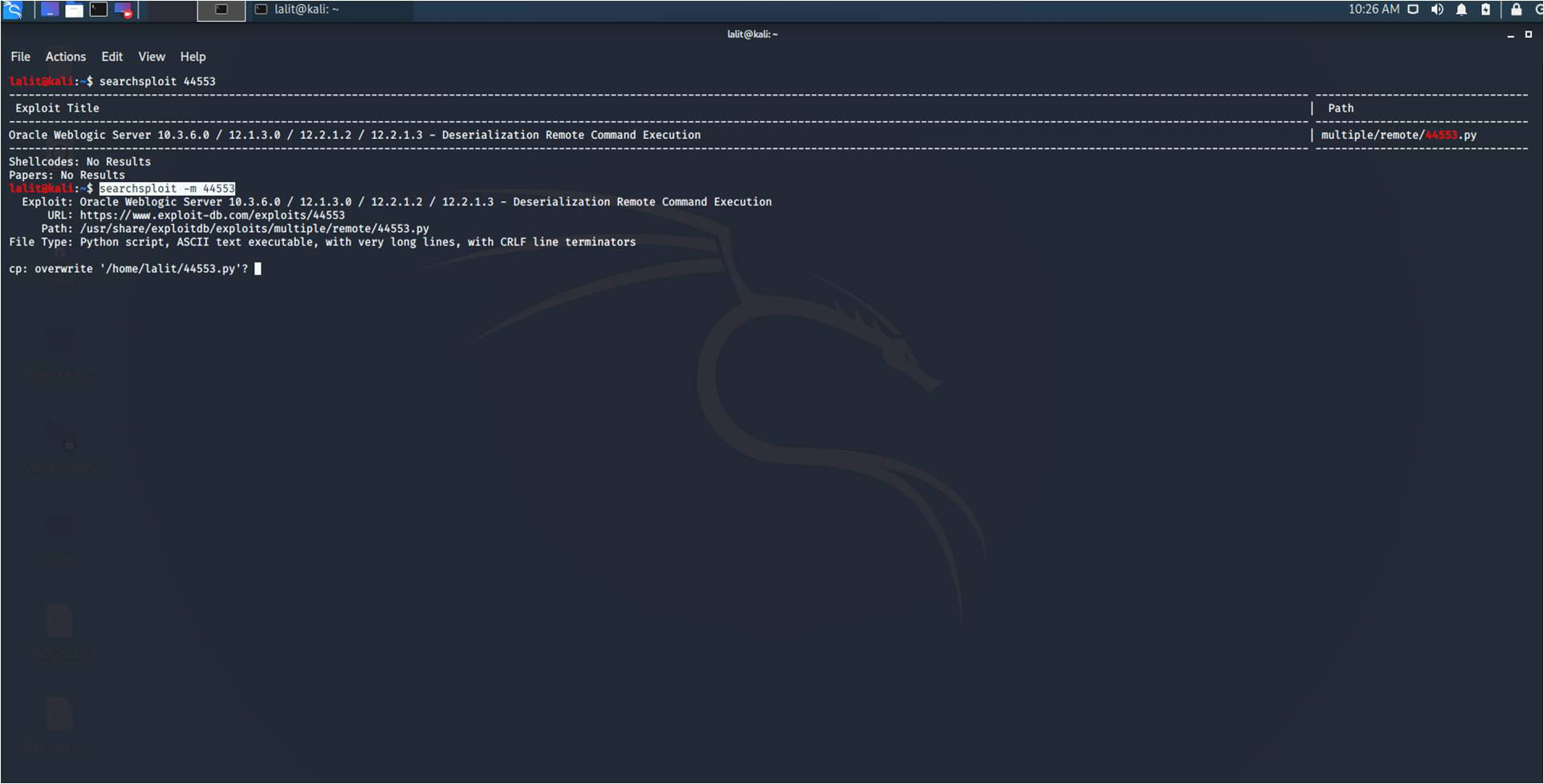
Using SearchSploit: 1. Basic Search - You can add any number of search terms you wish to look for. In the below image, we are searching for exploits containing the term "oracle" and "windows". In case you need help just type "searchsploit -h" in the terminal. By using -h, you can see all the options and features that are available.
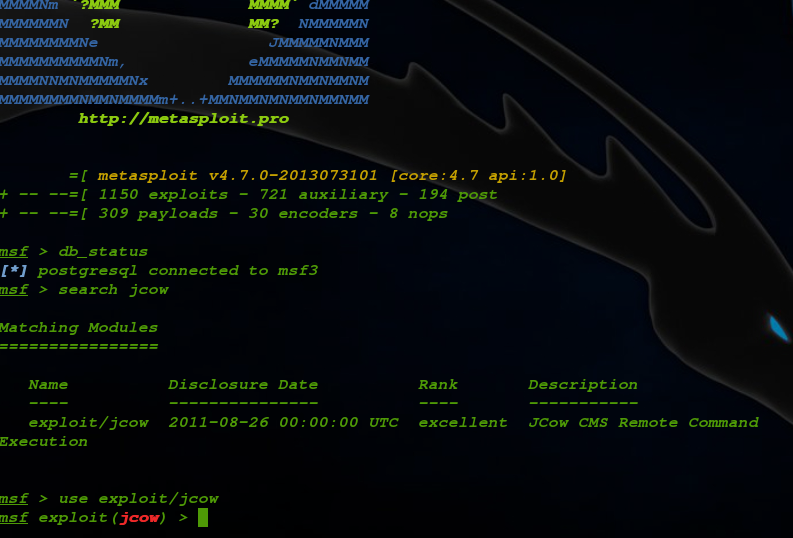
Hacking and Programming Cara Menambah Exploit Ke Metasploit di kali linux
A Kali Linux Live image on a CD/DVD/USB/PXE can allow you to have access to a full bare metal Kali install without needing to alter an already-installed operating system. This allows for quick easy access to the Kali toolset with all the advantages of a bare metal install. There are some drawbacks, as disk operations may slow due to the.

Encontrar Exploits en Kali Linux utilizando Searchsploit Alonso Caballero / ReYDeS
12. BeEF. BeEF (Browser Exploitation Framework) is yet another impressive tool. It has been tailored for penetration testers to assess the security of a web browser. This is one of the best Kali Linux tools because a lot of users do want to know and fix the client-side problems when talking about web security. 13.

how to install blueborne exploit in kali linux for blueborne attack easily YouTube
2. Once installed, you'll see the Oracle VM VirtualBox in your start menu, click on it to launch the VirtualBox application. 3. We'll also need to download and install the Oracle VM VirtualBox Extension Pack as it's required to run the Kali Linux Virtual Appliance: 4. Running the file will prompt you with a warning.

Cara exploit Sql Injection dengan Sqlmap di kali linux
How to Use Metasploit's Interface: msfconsole. To begin using the Metasploit interface, open the Kali Linux terminal and type msfconsole. By default, msfconsole opens up with a banner; to remove that and start the interface in quiet mode, use the msfconsole command with the -q flag. The interface looks like a Linux command-line shell.

Encontrar Exploits en Kali Linux utilizando Searchsploit Alonso Caballero / ReYDeS
Steps. Download Article. 1. Start up Kali and fire up the Terminal console. 2. Type ifconfig to display the interface and check your IP address. 3. Type msfvenom -l encoders to show the list of encoders. You will use x86/shikata_ga_nai as the encoder.